Cyber Risk Transformation – The Issue of 4
Runaway Trains.

Gautam Dev – May 16th, 2016
Part1: Establishing Context
A Necessary Yet Difficult Proposition:

Majority of the Information Security Officers across all industry spectrum tasked with policies and controls to help protect their enterprise ‘digital crown jewels’, will tell you that they understand well that a risk intelligence based program is the way forward to truly be successful in implementing a sound capability to resist or recover from a cyber-attack. However most of them will also tell you that it is a difficult proposition to make happen. Although, some I know have been brave enough to venture successful small steps past the hurdles.
The Runaway Train Problem:

#1 Increasing, Evolving, Industry regulations and standards, along with,
#2 Increasing, Evolving Business models, along with,
#3 Increasing, Evolving Cyber Security tools and Technology trends, along with,
#4 Increasing, Evolving variety and intensity of Cyber Breaches make it a tough ask for the ‘digital crown jewel safe keepers’ to come up with a plan which in their minds will past management muster and will be successful in ensuring that these ‘4 Runaway Trains’, increasing in varied velocity and chalking unknown routes, can be programmed to operate in a synchronized, visible fashion towards a measured, compliant, safe and ROI driven outcome.
Cracking the code:

Let’s begin by attempting an analogous decipher to the context.
The Proverbial Bookworm Syndrome:
Over our education lifetime, we have all sat through different varieties of board sponsored standardized tests and certifications. Over time for all of these the learning industry has prescribed a number of best practices and testing templates which, they suggest with qualified statistics, when one follows religiously will guide them to excelling in their goals. When one doesn’t get the desired results and are disappointed in how the results could be so discouraging when they complied with all that the doctor ordered. They have the course completion certificates to vouch for that.
The Minimal Saving Grace:

Now relatively, coming back to cyber reality, security controls and industry standards besides being mandatory, provide the ‘digital crown jewel safe keeper’ a way and means to set out their security posture, get measured and certified for compliance by auditors to prove they have done everything by the book and thus right. A breach happens but how could it they have the certifications to vouch for an expensive, exhaustive, secured and compliant posture.
The Cyber Elephant:

Yes, I may be oversimplifying this and being philosophical about a well-known paradigm. Often times though it becomes obvious that pointing to the elephant in the room which everyone knows exists but is overlooked for the fear of disrupting the norm, helps identify the problem and address all perspectives clearly. No, I am also not suggesting we disregard regulations and best practices. For one they are required and two it certainly is better to be compliant rather than not so and also be a victim of a cyber-attack. It’s another thing though, what might get called out to be non-compliant after a breach versus before it. This is the issue of The 1st Runaway Train about keeping up with increasing, evolving controls and best practices.
Swift & Informed Adaptability:

“A Law is only as effective in principle as its informed adaptability through swift policed enforcement in practice”. Security compliance and regulations should not be an impediment for a business to pursue innovative growth. A program that ensures swift and informed adaptability alleviating business concerns about risks from the get go will provide the most value and management support. Certifications, controls, standards and guidelines are all good things. Learning and evolving from past mistakes is an essential part of any form of judgement. There is no substitute to documented knowledge and subsequent understanding of what is a good practice. What is important though, for it to be applied successfully to a risk based program that supports business innovation, is finding the right balance between its compliant application with its informed, adaptive, responsive and practical enforcement at all times. This is the issue of The 2nd Runaway Train about adapting to increasing, evolving business models.
Finding the Problem to the Solutions:
The Cyber Security Technology Industry is growing at a brisk space. Why shouldn’t it, there is so much fear of the unknown that it bodes emergence of different technical answers for defining and preventing uncertainty to be the most practical form of successful economics. The economics of make hay while the sun is shining kind. This Cyber Security Technology Revolution by no means is a bad thing. History is evidence that all industrial revolutions from Mechanical to Digital have led to innovations helping improve quality of life, business and boosting global income and markets. Besides it has also just over the last few years given us some new, unique and powerful tools to work with while some older powerhouses have reworked their stack to adapt to a risk based landscape. So it’s a good thing. Where’s then the issue, the Issue of the 3rd Runaway Train, about increasing, emerging tools and technology trends. Remember the metaphor, no one shoe size fit all? The difference in this scenario is that we have a closet full of shoes with varied shapes, sizes, brands to choose from and for every occasion (/risk). Having a right measure for the correct number, size and shape of shoes that belong in our risk based closet becomes essential. In cyber terms that would mean establishing a measure for the organization’s unique risk posture and adaptability requirements first before spending our hard fought budget dollars while also drawing maximum value from existing investments.
Tug O’ Cyber War:

‘If ain’t broke, don’t fix’ goes another popular metaphor. Human race progressive as it is, though, thrives on overcoming challenges and breaking from the norm in our quest for evolution. From solving the Rubik’s cube, landing on moon, summiting the Everest, unraveling the mysteries of the Pyramids to breaking of atoms, we desire acquiring social, political and financial efficacy by hacking away from the status quo. This human one-upmanship trait, call it Herbert Spencer’s ‘Survival of the fittest’ or Darwin’s ‘Natural Selection’ theory, has set in motion a cyclic, cyber-warfare evolution:
Secure it – Learn it, Break it – Evolve and Secure it Stronger – Inherit, Evolve further and Break it again.
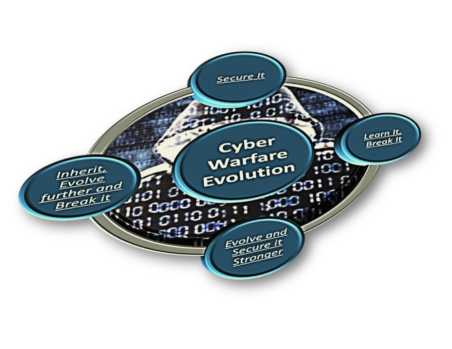
This Cyber one-upmanship between the good and the bad is evident from year on year statistics, which shows both a significant increase in Cyber Defense spending and also an increase in the number and intensity of Cyber Attacks. The continuous evolution of breaking techniques adapting and inheriting from the continuous evolution of security hardening techniques, is the Issue of the 4th Runaway Train.
The Day After Tomorrow:
For data breaches over just the last 3 years, industry analysts have put a dollar amount for each record breached at an average ranging from $175 of $220 per compromised record. This includes indirect costs pertaining to abnormal turnover or churn of customers and direct costs incurred due to security hardening by investing in more technologies or legal fees. The valuation and assumption that the data breached is for immediate purposes of profit from being sold in the identity fraud black market, is correct. The whole perspective however is myopic. Here’s one Big Data example of Why: Our next-gen Cyber Defense hopes rest on real time, big data analytic driven artificially intelligent systems. These when fueled by volumes of data will have self-learning and correcting capabilities to baseline normal situations and actors with a view to perform filtration of anomalous actions and content, thereby stopping an attempt to a breach. Standards, Best Practices, Regulations, Controls, the hacking industry can be correctly assumed to have our entire playbook. They have access to Cyber Security technologies in its current form along with knowledge of next-gen intelligent system concepts, publicly publicized and perceived to take effect in the future. All this combined provides these cyber villains with ready capability to evolve from previously successful breaching techniques and begin adapting their attacks towards newer intelligent system concepts by emulating baseline norms. Not to forget that just over a 3-year period the number of records breached and available within the hacking black market is approximately a whopping 3 Billion. So, while we approve, fund, develop, implement our next-gen cyber weaponry and then pump it with volumes of data for it to calibrate baselines, our cyber nemesis on the dark side is equipped with the technology know how and has access to ready fuel, the 3 billion records breached from various sources, to enrich and reverse engineer our next wave of Cyber Defense. Oh, and we will still have Dave (image below) on our side.
That last bit of humor brings us to a wrap for Part 1.
Part1 Synopsis:
Recognized the Challenge: Part 1, highlighted 4 core complex challenges faced by the industry while considering transformation to a successful Risk based Program.
- Practical application of Compliance and Best Practices to be adopted,
- Enabling Business innovation,
- Emerging tools and Technology trends,
- and Cyber Breach intensity.
Established a Win Theme: Earlier in the post when I first mentioned the issue of the 4 metaphorical Runaway Trains, increasing in varied velocity and chalking unknown routes. I wrote that for any Risk based program to pass muster it will need to ensure that these issues, be addressed in a synchronized and visible fashion towards providing a measured, compliant, safe and ROI driven outcome.
Provided Reasoning and Benchmark: In this 1st Part, before detailing a framework for addressing each issue, it was important to first baseline the reason behind the varied velocity and unknown course, followed by an explanation of its impact on the measure of complexity arising from it. With that purpose, the essay, provides a reasoning behind the existence and uniqueness of each issue and subsequently an explanation for what makes each of the 4 issues complex and unique to each organization considering a successful Risk based Program.
A Look Ahead: Building onward from Part 1, Part 2 will consider the benchmark considerations highlighted in the 1st part to address and define elements of transformation for:
- An Adaptable Risk Based Program Framework, and
- Its subsequent Governance.


